Azure provides a set of compute options, ranging from Virtual Machines, Container-based deployment support (includes AKS or Azure Kubernetes Services), Azure Web apps, Azure functions, etc.
Virtual Machines: Give you control over infrastructure as well as Operation systems.
When one is provisioning VMs, be aware of two types of downtimes that can occur.
Planned Maintenance: When Microsoft makes an update to the Azure platform, for example, security patches being deployed.
Unplanned Maintenance: There can be issues like power failures, which will cause the downtime
To handle these issues we have various options
Availability Sets: Availability sets allows you to manage update domain and fault domains.
An update domain is a group of virtual machines and underlying physical hardware that can be rebooted at the same time. When planned maintenance is performed on the Azure platform, only one update domain is rebooted at a time. This ensures that all VMs and associated hardware are not taken down at the same time.
A fault domain is a group of virtual machines that shares a common power source and a common network switch. When virtual machines are added to an availability set, they are distributed across up to three different fault domains in resource manager deployments, or across two fault domains in classic deployments.
Availability Zones: It is physically separate zones within an Azure region. There are usually three zones in one region. To increase the availability of your application, you should deploy it in more than one zone.
Multi-Region Deployment: Once can further deploy to multiple regions to avoid region failures.
Virtual Machine ScaleSet: Azure virtual machine scale sets let you create and manage a group of load-balanced VMs. You can set rules for scaling as CPU percent goes beyond 60%. In addition, one can set Load Balancer which helps manage traffic at layer 4, or Application Gateway which helps distribute traffic at layer 7.
Azure Functions: This helps serverless computing, one can use a consumption-based plan where you pay only for the time the function was running. But it has limitations like the function can run for a max of 10 minutes. One can upgrade to an App service plan to avoid these limitations.
Azure Logic Apps: You can create workflows, to create low code/ no code applications.
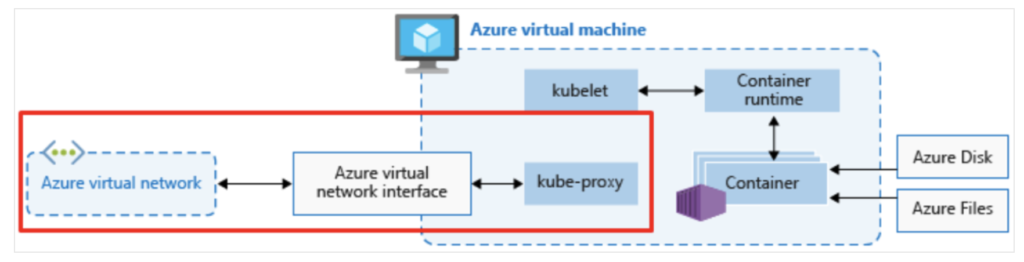
Azure Kubernetes Service: Azure implementation for managing Kubernetes and Container based deployments.
Azure Service Fabric: Another offering to manage container-based deployments, supports both synchronous and asynchronous applications.
Azure App Service: Works on the model where you get your code and directly deploy it on Azure, without worrying about deployment details. This supports deployment slots, for example, you can create stage and prod deployment slots, once you deploy and test on stage successfully, you can just swap with prod deployment.