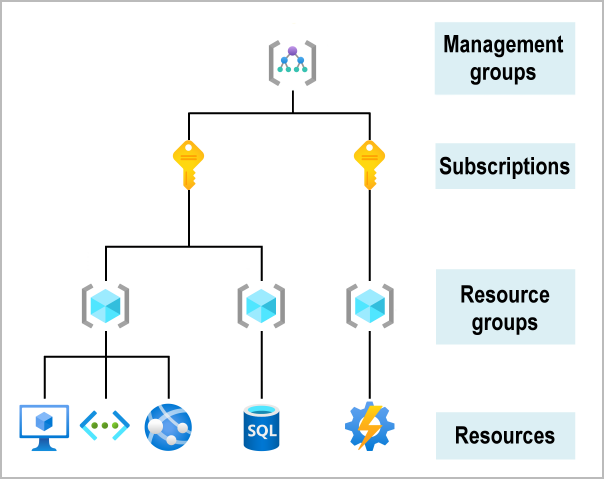
Azure API Management provides a set of services that can help users to manage API Lifecycle, i.e. Design. Mock, Deploy, Policy Management, Explore, Consume, and Monitor APIs.
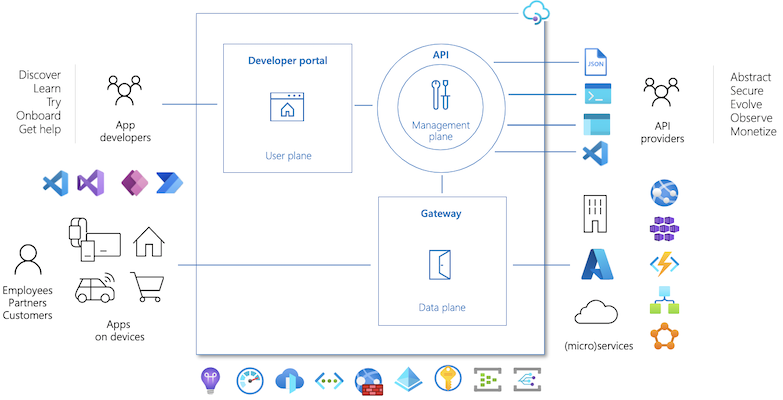
we can see there are three core components here. Developer portal helping consumers to discover, try out and onboard to services. Management Plane helps providers manage the API policies and monitor them. The gateway is the interface between consumer clients and provider applications.
API Gateway
The API gateway acts as a facade to the backend services, allowing API providers to abstract API implementations and evolve backend architecture without impacting API consumers. The gateway enables consistent configuration of routing, security, throttling, caching, and observability.
https://learn.microsoft.com/en-us/azure/api-management/api-management-key-concepts#api-gateway
To create API Gateway, you will need to go to Azure Portal -> API Management Service -> Create
Management Plane
API providers interact with the service through the management plane, which provides full access to the API Management service capabilities. Customers interact with the management plane through Azure tools including the Azure portal, Azure PowerShell, Azure CLI, a Visual Studio Code extension, or client SDKs in several popular programming languages.
https://learn.microsoft.com/en-us/azure/api-management/api-management-key-concepts#management-plane
If Gateway was about implementing policies in real-time, Management plane is about helping developers set these policies and interact with analytics dashboards via portal VC Code extension or other Azure interfaces.
Developer Portal
App developers use the open-source developer portal to discover the APIs, onboard to use them, and learn how to consume them in applications.
https://learn.microsoft.com/en-us/azure/api-management/api-management-key-concepts#developer-portal
The developer portal allows consumers to search for APIs, explore them, consume them and view analytics from the consumer side.